New Phishing Attack Bypasses 2FA Using Real-Time Interception

Sarah Johnson
March 31, 2025
Brief
Astaroth, a new advanced phishing kit, bypasses two-factor authentication by intercepting credentials and session cookies in real-time, posing serious threats to online account security.
Phishing attacks have become a constant threat, and while many of us can recognize the more obvious attempts, a new and advanced phishing kit called Astaroth is taking things to a dangerous new level. This tool is capable of bypassing two-factor authentication (2FA) entirely, using real-time credential interception and session hijacking.
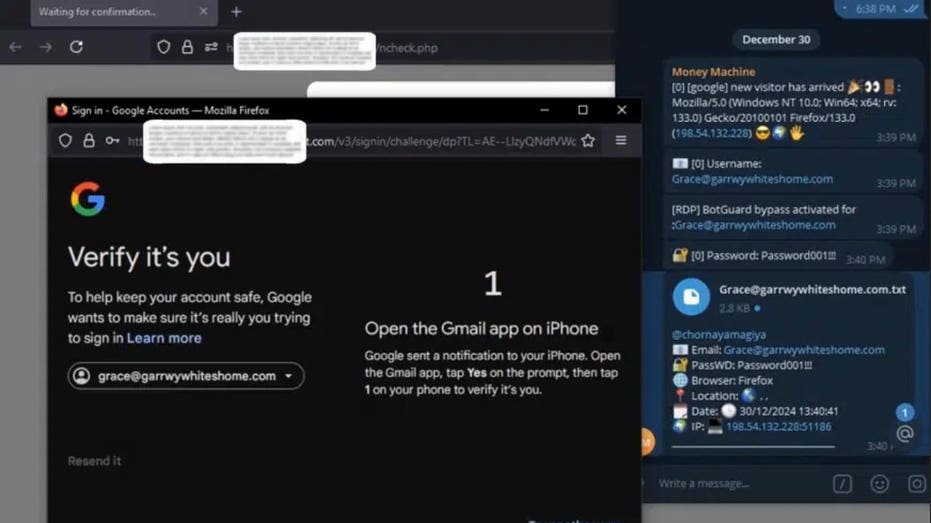
Unlike traditional phishing methods that rely on fake login pages, Astaroth operates as a middleman between your device and legitimate authentication services such as Gmail, Yahoo, and Microsoft. It intercepts data in real-time, scooping up usernames, passwords, and even one-time authentication codes, leaving no room for 2FA to save the day.
The attack begins with a phishing link that directs victims to a malicious site mimicking a legitimate one. With valid SSL certificates in place, there are no immediate red flags. Once you enter your details, including device info and IP address, Astaroth captures them before forwarding the request to the actual website, ensuring the victim remains unaware of the breach.
Here’s the kicker: Astaroth doesn’t just stop at stealing login credentials. It also snatches session cookies, the tiny data packets that keep users logged in after authentication. By injecting these cookies into their own browsers, attackers can bypass both passwords and 2FA, gaining seamless account access.
According to cybersecurity firm SlashNext, Astaroth stands out due to its ability to intercept credentials in real-time, automate attacks, and resist takedown efforts. Traditional phishing kits rely on tricking victims into entering credentials on fake login pages, but Astaroth eliminates that step, making it even more insidious.
Adding to its appeal for cybercriminals, Astaroth offers features like bulletproof hosting to evade law enforcement, regular updates to bypass security patches, and a structured payment model. For $2,000, buyers get six months of updates, and the creators even let potential buyers test the kit before purchasing. It’s widely distributed through platforms like Telegram and underground cybercrime forums, making it difficult for authorities to track its spread.
Signs You May Be Compromised:
- Unexpected account logins or security alerts
- Being mysteriously logged out of accounts
- Password changes or settings updates you didn’t make
- Slow system performance or unusual behavior
- Strange browser activity
- Unfamiliar programs or scripts running in the background
How to Protect Yourself:
1) Avoid unknown links and use strong antivirus software: Astaroth, like most malware, requires user interaction—clicking a link, visiting a malicious website, and entering credentials. Avoiding suspicious links and using robust antivirus software can prevent such attacks. Strong antivirus solutions can also detect phishing attempts and ransomware scams, safeguarding your personal data.
2) Double-check websites: Always verify website addresses. Instead of clicking on links in emails or messages, manually type the URL or use trusted bookmarks to minimize the risk of landing on fraudulent sites.
3) Keep your devices updated: Regular updates for your operating system and applications close vulnerabilities that malware might exploit, making it harder for attackers to gain access to your device.
4) Avoid typing passwords: Whenever possible, use passwordless login methods such as passkeys, Google Sign-In, or Apple Sign-In. These methods rely on cryptographic keys or secure tokens, making it harder for attackers to intercept your login information.
Astaroth is a stark reminder of how quickly cybercriminals are advancing. While traditional security measures like 2FA are no longer foolproof, adopting passwordless logins, staying updated, and staying informed can help protect against these evolving threats. Cybersecurity is a moving target, and awareness is your best shield.
What do you think governments and companies should do to tackle sophisticated cyber threats like Astaroth? Share your thoughts with us at Cyberguy.com/Contact.
Topics
Editor's Comments
This Astaroth phishing kit feels like it belongs in a cybercrime thriller—it’s that advanced and sinister. The way it can hijack an entire session and make 2FA irrelevant is both fascinating and terrifying. It’s a reminder that while we build better locks, someone’s always working on a better lock pick. Stay sharp, folks!
Like this article? Share it with your friends!
If you find this article interesting, feel free to share it with your friends!
Thank you for your support! Sharing is the greatest encouragement for us.